The design of operating system architecture traditionally follows the separation of concerns principle. This principle suggests structuring the operating system into relatively independent parts that provide simple individual features, thus keeping the complexity of the design manageable.
1. Simple Structure:
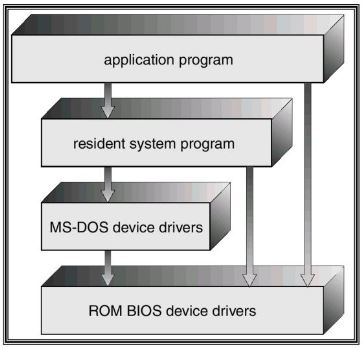
- There are several commercial systems that don’t have a well-defined structure such operating systems begin as small, simple & limited systems and then grow beyond their original scope.
- MS-DOS is an example of such a system. It was not divided into modules carefully.
- Another example of limited structuring is the UNIX operating system.
- There was no CPU Execution Mode (user and kernel), so errors in applications could cause the whole system to crash.
2. Monolithic Approach:
- A monolithic design of the operating system architecture makes no special accommodation for the special nature of the operating system. Although the design follows the separation of concerns, no attempt is made to restrict the privileges granted to the individual parts of the operating system.
- The entire operating system executes with maximum privileges.
- The communication overhead inside the monolithic operating system is the same as the communication overhead inside any other software, considered relatively low.
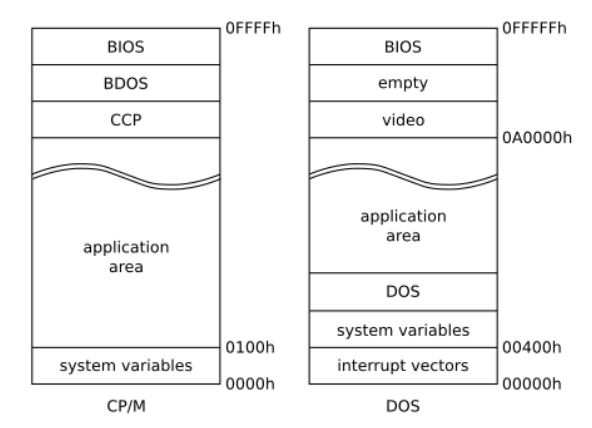
- CP/M and DOS are simple examples of monolithic operating systems. Both CP/M and DOS are operating systems that share a single address space with the applications. In CP/M, the 16-bit address space starts with system variables and the application area and ends with three parts of the operating system, namely CCP (Console Command Processor), BDOS (Basic Disk Operating System), and BIOS (Basic Input/Output System). In DOS, the 20-bit address space starts with the array of interrupt vectors and the system variables, followed by the resident part of DOS and the application area, and ends with a memory block used by the video card and BIOS.
3. Layered approach:
In the layered approach, the OS is broken into a number of layers (levels) each built on top of lower layers. The bottom layer (layer 0) is the hardware & top most layer (layer N) is the user interface. The main advantage of the layered approach is modularity.
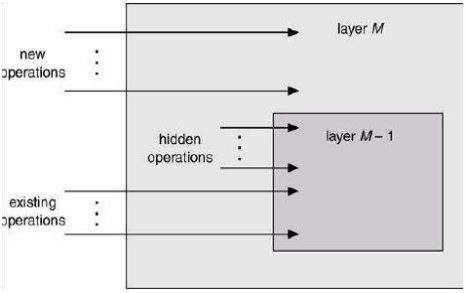
- The layers are selected such that each user functions (or operations) & services of only the lower layer.
- This approach simplifies debugging & system verification, i.e. the first layer can be debugged without concerning the rest of the system. Once the first layer is debugged, its correct functioning is assumed while the 2nd layer is debugged & so on.
- If an error is found during the debugging of a particular layer, the error must be on that layer because the layers below it are already debugged. Thus the design & implementation of the system is simplified when the system is broken down into layers.
- Each layer is implemented using only operations provided by lower layers. A layer doesn’t need to know how these operations are implemented; it only needs to know what these operations do.
- The layered approach was first used in the operating system. It was defined in six layers.
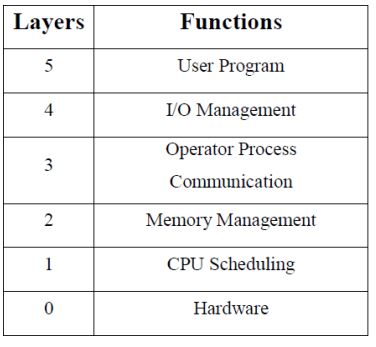
The main disadvantage of the layered approach is:
- The main difficulty with this approach involves the careful definition of the layers because a layer can use only those layers below it. For example, the device driver for the disk space used by the virtual memory algorithm must be at a level lower than that of the memory management routines, because memory management requires the ability to use the disk space.
- It is less efficient than a non-layered system (Each layer adds overhead to the system call & the net result is a system call that takes longer time than on a nonlayered system).
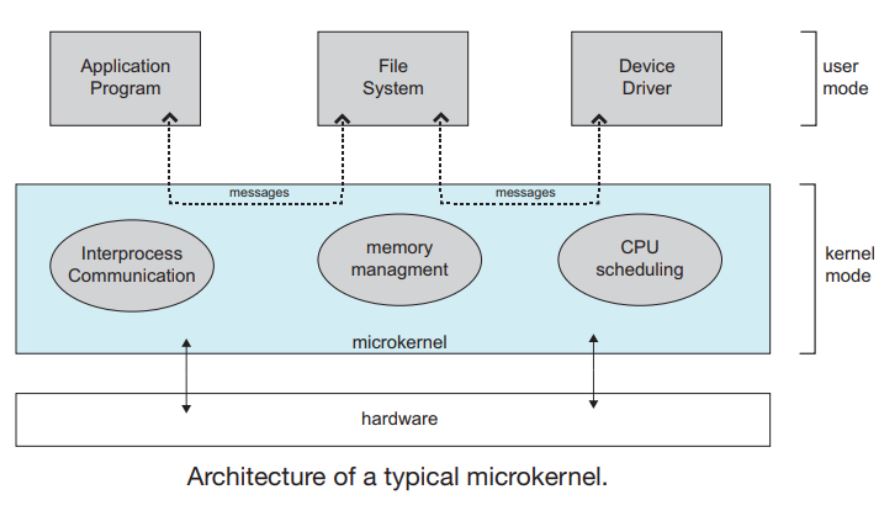
4. Microkernel approach:
- This structures the operating system by removing all nonessential portions of the kernel and implementing them as system and user-level programs.
- Generally, they provide minimal process and memory management, and a communications facility.
- Communication between components of the OS is provided by message passing.
The benefits of the microkernel are as follows:
- Extending the operating system becomes much easier.
- Any changes to the kernel tend to be fewer since the kernel is smaller.
- The microkernel also provides more security and reliability. The main disadvantage is poor performance due to increased system overhead from message passing.
5. Virtual Machines:
- A virtual machine takes the layered approach to its logical conclusion.
- It treats hardware and the operating system kernel as though they were all hardware.
- A virtual machine provides an interface identical to the underlying bare hardware.
- The operating system creates the illusion of multiple processes, each executing on its own processor with its own (virtual) memory.
- The resources of the physical computer are shared to create virtual machines.
- CPU scheduling can create the appearance that users have their own processors.
- Spooling and a file system can provide virtual card readers and virtual line printers.
- A normal user time-sharing terminal serves as the virtual machine operator’s console.
Advantages and Disadvantages of Virtual Machines:
- The virtual-machine concept provides complete protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources.
- A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the virtual machine, instead of on a physical machine and so does not disrupt normal system operation.
- The virtual machine concept is difficult to implement due to the effort required to provide an exact duplicate to the underlying machine.
Drawback:
- Virtual Machine includes increased system overhead which is due to the simulation of virtual machine operation heavily.
- The efficiency of VM OS depends upon the number of operations that must be simulated by the VM monitor.
