A VLAN, known as a virtual local area network, is a group of connected devices offering all the capabilities typically associated with a local area network (LAN). There are a few differences between a normal LAN and a VLAN; the most notable is VLAN devices don’t have to be on the same network or physically connected to operate.
In a VLAN, device connections are created logically, which means the network is more flexible than a LAN. It also offers flexibility in making changes, as the physical location of each device does not impact VLAN connections. VLANs are an alternative to LANs because they offer greater scalability, better security, and improved network management.
In simple terms, a VLAN is a set of workstations within a LAN that can communicate with each other as though they were on a single, isolated LAN. What does it mean to say that they “communicate with each other as though they were on a single, isolated LAN”?
Among other things, it means that:
- Broadcast packets sent by one of the workstations will reach all the others in the VLAN
- Broadcasts sent by one of the workstations in the VLAN will not reach any workstations that are not in the VLAN
- Broadcasts sent by workstations that are not in the VLAN will never reach workstations that are in the VLAN
- The workstations can all communicate with each other without needing to go through a gateway. For example, IP connections would be established by ARPing for the destination IP and sending packets directly to the destination workstation—there would be no need to send packets to the IP gateway to be forwarded on.
- The workstations can communicate with each other using non-routable protocols.
Advantages of VLANs
In a regular LAN, all connected devices must be physically present in a specific location. If a user moves to another geographical destination, the network infrastructure must be altered. In a VLAN environment, however, there are no restrictions on the location of the connected devices, which means devices can be configured on a central basis no matter where they are. This has obvious benefits for network management, affording IT administrators increased flexibility and fewer limitations.
Employing a VLAN has advantages in the following areas:
- Network performance: Using a VLAN can result in improved network performance without the need to make physical alterations to your network. You can establish individual VLANs for each group of users, thereby compartmentalizing your traffic.
- Security: By dividing users into distinct groups, VLANs can improve security. In the event of a cyberattack, the impact is limited to the VLAN where the attack originated. This means users of other VLAN groups can continue to access their network and their work.
- Fault management: Using VLANs also improves fault management. Because users work in small groups, identifying the root cause of an issue is much easier. Finding the source of the issue is as simple as locating the group it originated from, narrowing down the potential causes of the problem. Additionally, with users connected in these small groups, troubleshooting is more effective.
- VLANs enable logical grouping of end-stations that are physically dispersed on a network.When users on a VLAN move to a new physical location but continue to perform the same job function, the end-stations of those users do not need to be reconfigured. Similarly, if users change their job functions, they need not physically move: changing the VLAN membership of the end-stations to that of the new team makes the users’ end-stations local to the resources of the new team.
- VLANs reduce the need to have routers deployed on a network to contain broadcast traffic.Flooding of a packet is limited to the switch ports that belong to a VLAN.
- Confinement of broadcast domains on a network significantly reduces traffic.By confining the broadcast domains, end-stations on a VLAN are prevented from listening to or receiving broadcasts not intended for them. Moreover, if a router is not connected between the VLANs, the end-stations of a VLAN cannot communicate with the end-stations of the other VLANs.
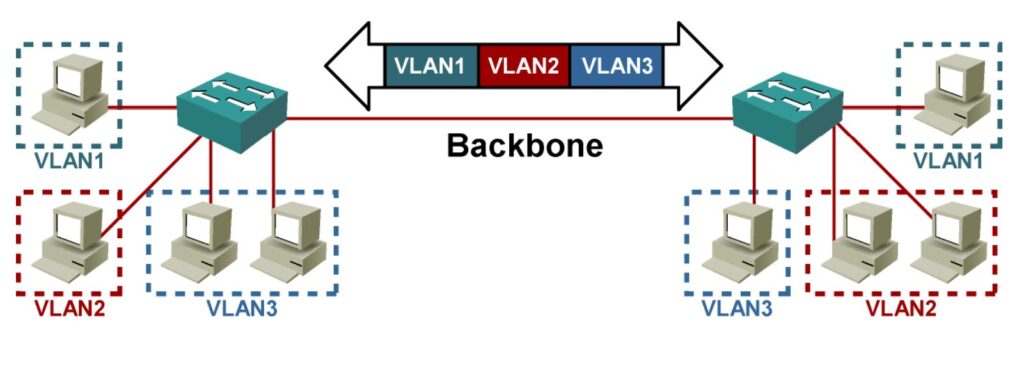
Before VLAN:
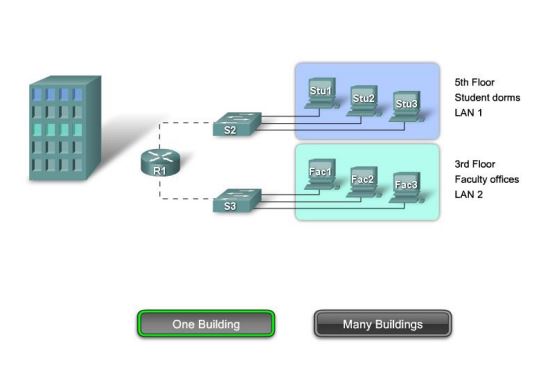
After VLAN:
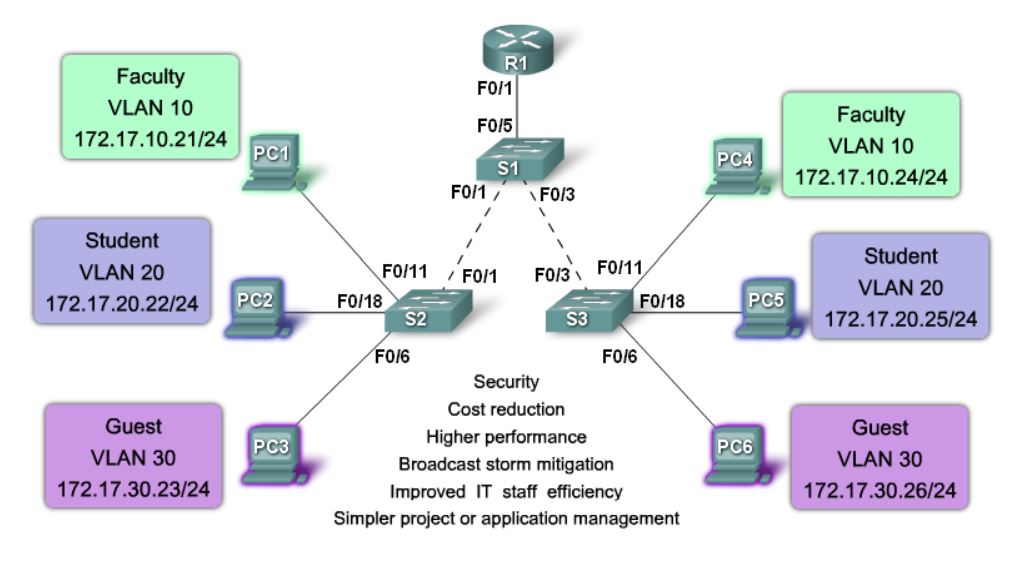
How to add a VLAN:
| Cisco IOS CLI Command Syntax | |
|---|---|
| Switch from privileged EXEC mode to global configuration mode. | #configure terminal |
Create a VLAN. VLAN id is the VLAN number that is to be created. Switches to VLAN configuration mode for VLAN vlan id. | (config)#vlan vlan id |
| (Optional) Specify a unique VLAN name to identify the VLAN. If no name is entered in the VLAN number, padded zeros are appended to the word ‘VLAN’, for example, VLAN0020. | (config-vlan) #name vlan name |
| Return to privileged EXEC mode. You must end your configuration session for the configuration to be saved in the vlan.dat file and for the configuration to take effect. | (config-vlan) #end |
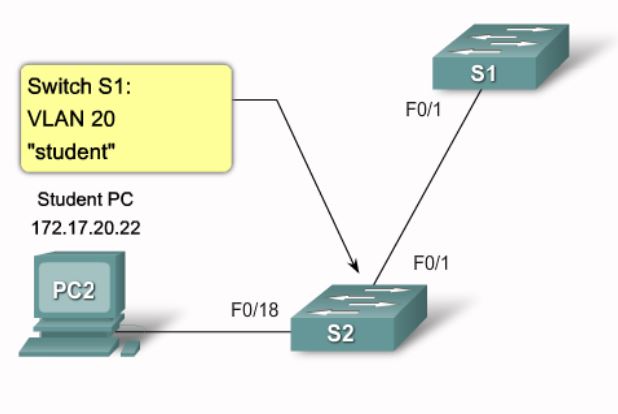
S1#configure terminal
S1(config)#vlan 20
S1(config-vlan)#name student
S1(config-vlan)#end
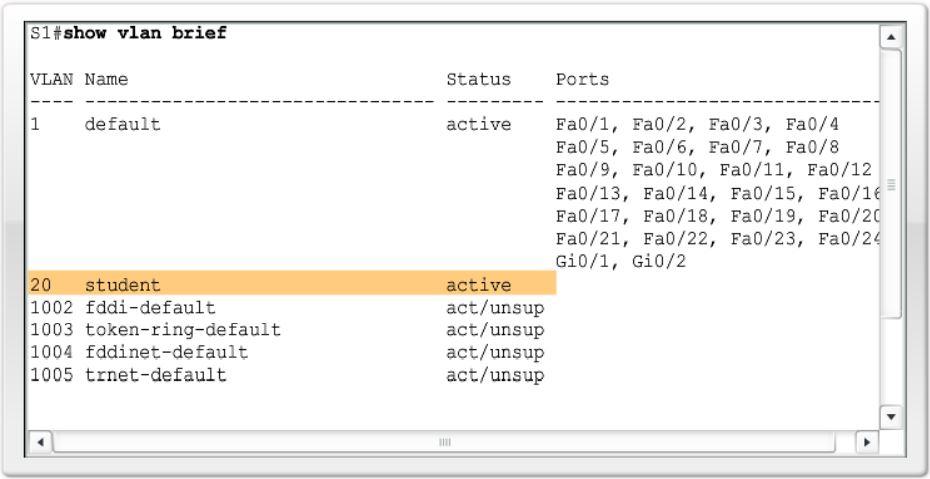
Access ports
A port that carries the data of only one VLAN:
configure terminal ##Enter global configuration mode
(config)#interface id ##Enter the interface to assign the VLAN (config-if)#switchport mode access ##Define the VLAN membership mode for the port (config-if)#switchport access vlan vlan id ##Assign the port to a VLAN (config-if)#end ##Return to priviledge EXEC mode.
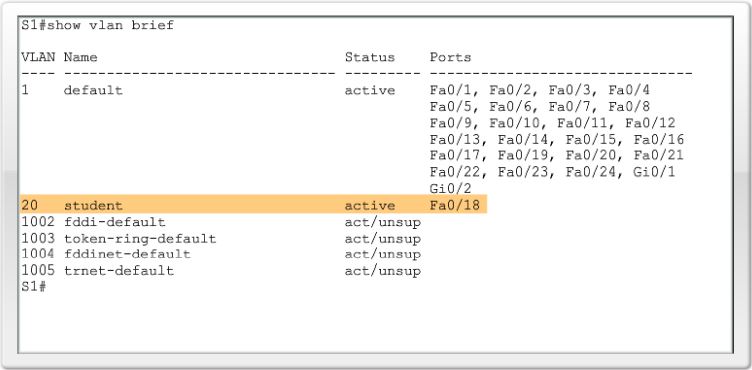
S1#configure terminal S1(config)#interface F0/18 S1(config-vlan)#switchport mode access S1(config-vlan)#switchport access vlan 20 S1(config-vlan)#end
Trunk links:
A port that carries traffic from different VLANs simultaneously
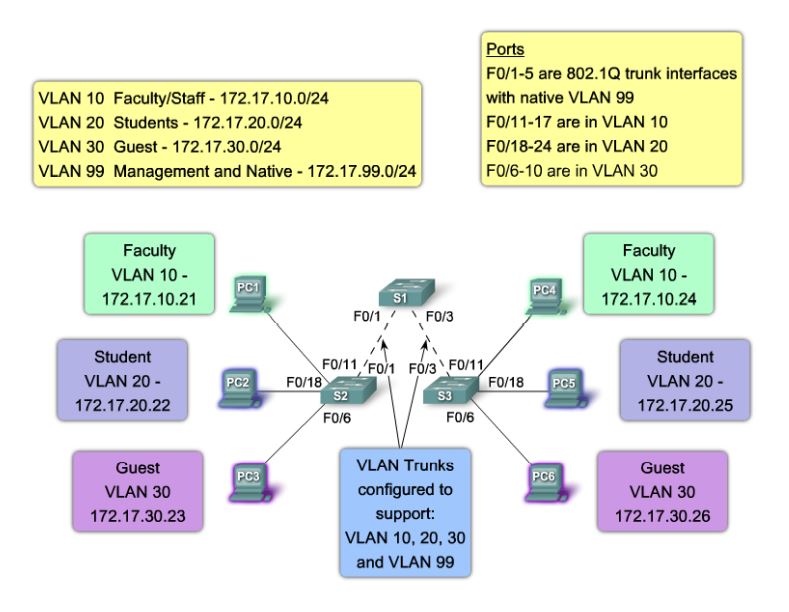
Trunk links: