A network access control list (ACL) is made up of rules that either allow access to a computer environment or deny it. In a way, an ACL is like a guest list at an exclusive club. Only those on the list are allowed in the doors. This enables administrators to ensure that, unless the proper credentials are presented by the device, it cannot gain access.
What are ACLs?
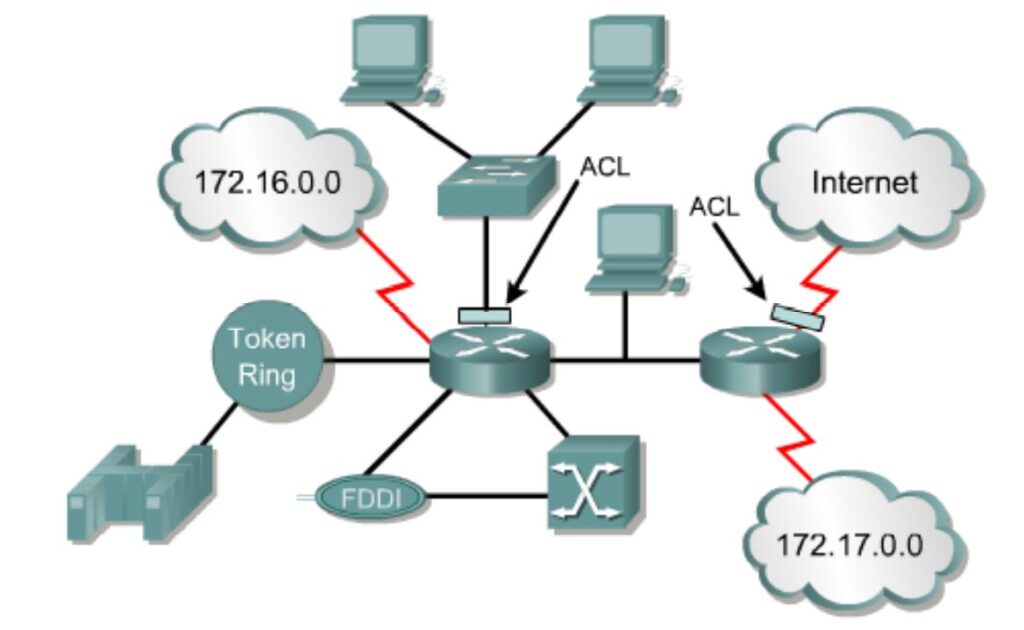
- ACLs are lists of conditions that are applied to traffic traveling across a router’s interface, these lists tell the router what types of packets to accept or deny.
- Acceptance and denial can be based on specified conditions.
- ACLs can be created for all routed network protocols, such as Internet Protocol (IP) and Internetwork Packet Exchange (IPX).
- ACLs can be configured at the router to control access to a network or subnet.
- Some ACL decision points are the source and destination addresses, protocols, and upper-layer port numbers.
- ACLs must be defined on a per protocol, per direction, or per port basis.
There are two basic kinds of ACLs:
- Filesystem ACLs: These work as filters, managing access to directories or files. A filesystem ACL gives the operating system instructions as to the users that are allowed to access the system, as well as the privileges they are entitled to once they are inside.
- Networking ACLs: Networking ACLs manage access to a network. To do this, they provide instructions to switches and routers as to the kinds of traffic that are allowed to interface with the network. They also dictate what each user or device can do once they are inside.
For more detail : Access Control List (ACL) in Networking
Reasons to Create ACLs
The following are some of the primary reasons to create ACLs:
- Limit network traffic and increase network performance.
- Provide traffic flow control.
- Provide a basic level of security for network access.
- Decide which types of traffic are forwarded or blocked at the router interfaces.
- For example: Permit e-mail traffic to be routed, but block all telnet traffic. Allow an administrator to control what areas a client can access on a network.
- If ACLs are not configured on the router, all packets passing through the router will be allowed onto all parts of the network.
How ACLs Filter Traffic
It acts as the gatekeeper of your network by regulating all incoming and outgoing data packets. The ACL works according to to set rules and checks all incoming and outgoing data to determine whether it complies with these rules.
Picture a bouncer at a club, checking to see if your name is on a list. If you’re on the list, you automatically go in and have access to the main floor. If you’re on the VIP list, you can go to the main floor and the VIP lounge. If you’re not on the list, the bouncer can choose whether or not to let you in based and where you’re allowed to go.
Ideally, your systems administrator will configure the ACL in a manner that allows the free flow of mission-critical data while simultaneously blocking off potentially dangerous traffic and updates at the router level, denying access to your private network. ACLs offer reasonably good security without sacrificing performance for important online applications and cloud services.
Creating ACLs
ACLs are created in the global configuration mode. There are many different types of ACLs including standard, extended, IPX, AppleTalk, and others. When configuring ACLs on a router, each ACL must be uniquely identified by assigning a number to it. This number identifies the type of access list created and must fall within the specified range of numbers that is valid for that type of list.
Command:
The access-list command:
Router(config)#access-list access-list-number {permit | deny} {test-conditions}
The permit or deny term in the global ACL statement indicates how packets that meet the test conditions are handled by Cisco IOS software. The permit usually means the packet will be allowed to use one or more interfaces that you will specify later. The final term or terms specifies the test conditions used by the ACL statement.
The IP access-group command:
Next, you need to apply ACLs to an interface by using the access-group command, as in this example:
Router(config-if)#{protocol} access-group access-list-number {in | out}
All the ACL statements identified by access-list-number are associated with one or more interfaces. Any packets that pass the ACL test conditions can be permitted to use any interface in the access group of interfaces.
ACL Example:
Router(config)#
access-list 2 deny 172.16.1.1
access-list 2 permit 172.16.1.0 0.0.0.255
access-list 2 deny 172.16.0.0 0.0.255.255
access-list 2 permit 172.16.1.0 0.255.255.255
interface ethernet 0
ip access-group 2 in
Basic Rules for ACLs:
These basic rules should be followed when creating and applying access lists:
- One access list per protocol per direction.
- Standard IP access lists should be applied closest to the destination.
- Extended IP access lists should be applied closest to the source.
- Use the inbound or outbound interface reference as if looking at the port from inside the router.
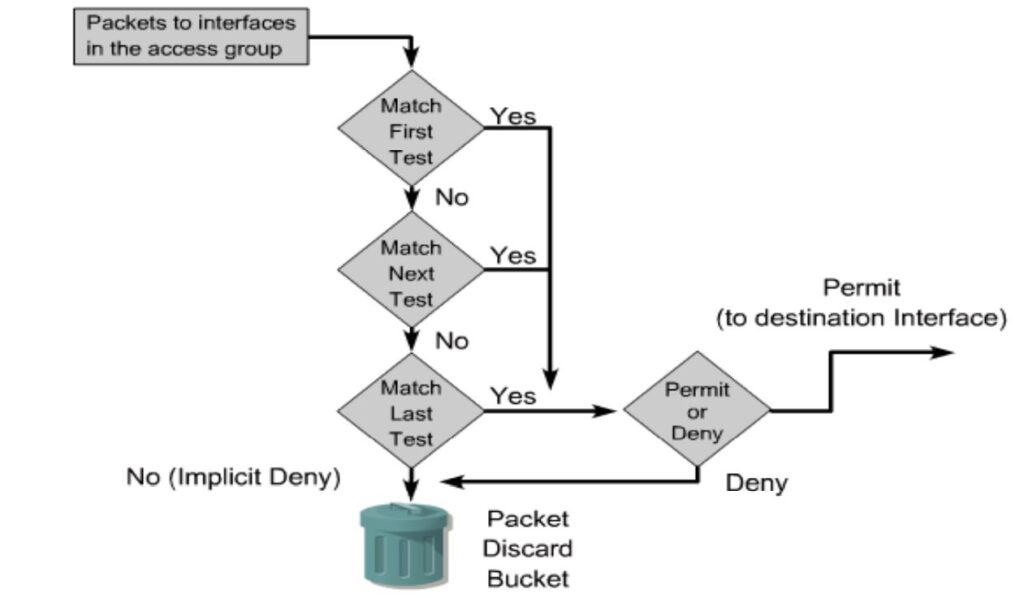
- Statements are processed sequentially from the top of the list to the bottom until a match is found, if no match is found then the packet is denied.
- There is an implicit deny at the end of all access lists. This will not appear in the configuration listing.
- Access list entries should filter in order from specific to general.
- Specific hosts should be denied first, and groups or general filters should come last. Never work with an access list that is actively applied.
- New lines are always added to the end of the access list.
- Ano access-list « command will remove the whole list. It is not possible to selectively add and remove lines with numbered ACLs.
- Outbound filters do not affect traffic originating from the local router.
Verifying ACLs:
There are many show commands that will verify the content and placement of ACLs on the router.
The show IP interface command displays IP interface information and indicates whether any ACLs are set.
The show access-lists command displays the contents of all ACLs on the router.
show access-list 1 #shows just access-list 1.
The show running-config command will also reveal the access lists on a router and the interface assignment information.

Pingback: Types of ACLs in Networking - Youngster Company